Title : IPD: Detecting Traffic Ingress Points at ISPs
Authors : Stefan Mehner (University of Kassel); Helge Reelfs (Brandenburg University of Technology); Ingmar Poese (BENOCS); Oliver Hohlfeld (University of Kassel)
Scribe: Xing Fang (Xiamen University)
Background
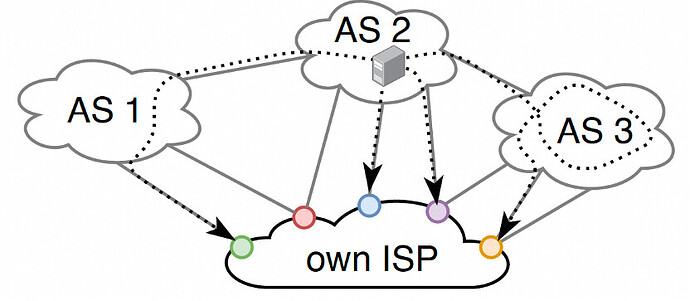
Detecting ISP traffic entry points is essential for network operations, such as identifying traffic sources during ISP link overloads. Challenges include the presence of multiple traffic entry points controlled by external AS policies, leading to asymmetries with BGP announcements, and the frequent changes in traffic entry points requiring real-time detection.
Implementation
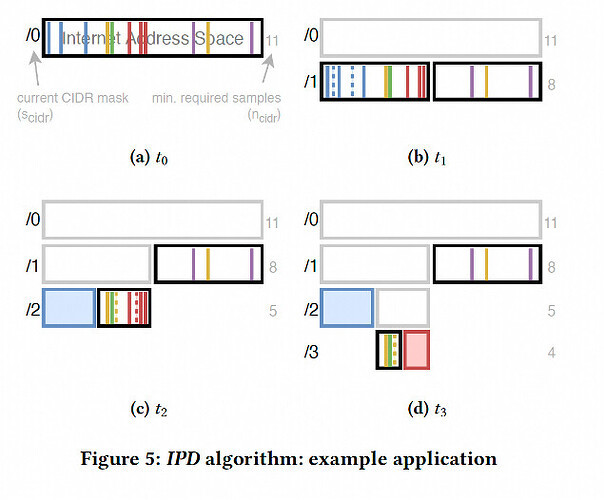
The paper presents IPD, a real-time ISP entry detection algorithm. IPD samples traffic flows at boundary routers and uses a divide-and-conquer approach to identify entry points. The process involves:
-
Initial Assessment: Treat all address spaces as a single block and collect traffic data.
-
Partitioning: Divide address spaces when traffic exceeds a threshold.
-
Entry Identification: Determine entry points based on traffic volume exceeding half the threshold in subdivided spaces.
-
Refinement: Continue division until the address space is accurately defined or reaches a set limit, like /28.
IPD ensures efficiency and accuracy by sampling flows, synchronizing time, and using parameters such as traffic thresholds and maximum space limits.
Evaluation
IPD was evaluated using synthetic data and six years of real ISP data, achieving over 90% detection accuracy. Key findings include:
-
Accuracy Limitations: Despite high accuracy, achieving 100% is challenging due to burst traffic, noise, and load-balancing imbalances.
-
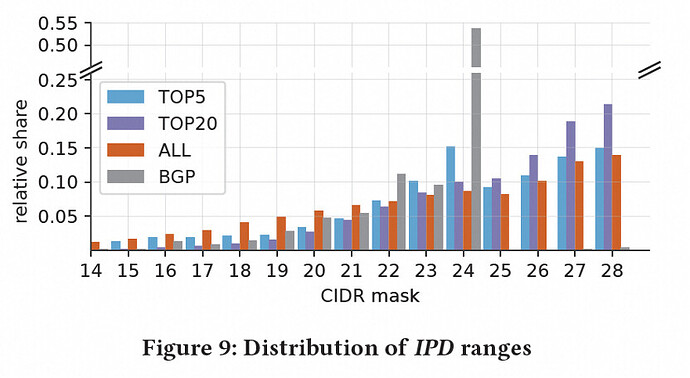
BGP Discrepancies: Differences between IPD-determined and BGP-announced address spaces arise from the dynamic nature of traffic and static BGP configurations.
-
Dynamic Traffic Handling: IPD adapts to traffic variations, with address spaces merging during low traffic and expanding during peaks.
-
Traffic Stability: Long-term stable traffic often shows substantial flow volumes within address spaces.
-
Asymmetry Issue: Significant discrepancies between traffic entry points and BGP announcements highlight BGP’s limitations for inferring entry points.
Q&A
Q1: Should IPD be run frequently, like every minute, or can it be done at longer intervals?
A1: While IPD can be run every minute and the results aggregated into 5-minute bins in practice, the resource consumption is low enough that running it frequently is not an issue. It can be adjusted based on specific needs without being a challenge in production.
Q2: How do you handle significant traffic changes hour by hour, and do you track different types of traffic?
A2: We only track high-volume sources and are not focused on different types of traffic. Our interest lies in premises with high traffic volume rather than differentiating traffic types.
Q3: How do you handle situations where traffic overflows from one ingress point to another, such as in load-balancing scenarios?
A3: There is a mechanism in place for detecting such overflows, ensuring proper traffic management and load balancing.
Personal Thoughts
IPD’s innovative divide-and-conquer algorithm effectively handles large volumes of ISP traffic data, but its accuracy is limited by statistical methods and exceptional traffic conditions. Exploring machine learning approaches could improve accuracy, and privacy-preserving techniques might offer insights without compromising ISP confidentiality. Future work should address these aspects to enhance detection performance.