Title: Reliable and Decentralized Certificate Revocation via DNS: The Case for RevDNS
Author: Protick Bhowmick (Virginia Tech USA), Dave Levin (University of Maryland
USA), Taejoong Chung (Virginia Tech USA)
Scribe: Kexin Yu (Xiamen University)
Introduction
The paper addresses the centralization and inefficiencies of OCSP (Online Certificate Status Protocol) used for certificate revocation in PKI (Public Key Infrastructure). It introduces RevDNS, a DNS-based system that utilizes DNSSEC for decentralized and efficient certificate revocation, improving performance and privacy.
Key Idea and Contribution
The main contribution of the paper is the RevDNS system, which offers a decentralized, efficient, and privacy-preserving method for certificate revocation. It eliminates the centralization risks of CDNs in OCSP, enhances performance through DNS caching, and reduces the operational burden on CAs. The paper also provides valuable measurements on the centralization of OCSP responses via CDNs and demonstrates the feasibility of RevDNS for large-scale deployment.
Evaluation
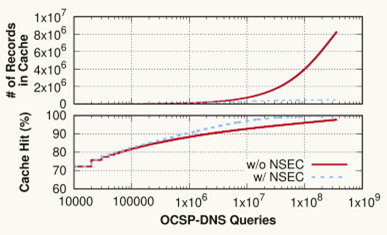
The paper provides a thorough evaluation of RevDNS’s performance and scalability:
- RevDNS can handle up to 612 million certificates for a major CA (e.g., Let’s Encrypt) using just 345 MB of DNS zone data.
- RevDNS significantly reduces latency, with 99.8% of revocation checks being served from cache by DNS resolvers. This avoids the need for repeated queries to Certificate Authorities, improving efficiency.
- The use of DNSSEC and NSEC records ensures that certificate revocation data is handled without exposing more information than standard DNS traffic, preserving user privacy.

Question
Q: Why don’t you finish the TLS handshaking they you update the data and the same time you do the verification checking?
A: If certificate status verification is delayed until after the TLS handshake is complete (i.e., completing the handshake and initiating communication before checking certificate validity), any subsequent discovery of certificate issues (such as revocation) cannot “retroactively” revoke or invalidate the already transmitted communication data, thereby creating security risks.
Personal Thoughts
RevDNS offers a practical solution to the challenges of certificate revocation in PKI systems, improving decentralization, performance, and privacy. Its reliance on DNSSEC is a key strength but also presents a challenge in adoption, as DNSSEC deployment is still limited. Despite this, RevDNS has great potential for improving the efficiency and security of certificate revocation in the future.
